Disable Teams app user requests (hide blocked Teams apps)
It finally happened! Microsoft released tooling to disable the user request functionality for Teams apps, introduced in August 2022, and consequentially hide blocked Teams apps from the Teams app store again. Microsoft announced the release of this new capability quietly, without a dedicated Message Center announcement, only updating the old MC411463 post which introduced the user request feature in the first place. In the following, I will describe two methods to disable the user request feature using Graph Explorer and PowerShell.
Using Graph Explorer
Navigate to Graph Explorer in your browser of choice.
- Sign in to your tenant
2. Chose method GET and enter the following URL:
https://graph.microsoft.com/beta/teamwork/teamsAppSettingsYou will be prompted to consent to the permissions to use the endpoint. The only required permission is TeamworkAppSettings.ReadWrite.All. When the required permission is granted, you will get a response similar to this:
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#teamwork/teamsAppSettings/$entity",
"id": "...",
"allowUserRequestsForAppAccess": true,
"isChatResourceSpecificConsentEnabled": true
}To disable the user requests and consequentially hide blocked apps in the Teams app store, select method PATCH and add the following request body:
{
"@odata.type": "#microsoft.graph.teamsAppSettings",
"allowUserRequestsForAppAccess": "false"
}To validate if the configuration was successful, simply run the GET method again.
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#teamwork/teamsAppSettings/$entity",
"id": "...",
"allowUserRequestsForAppAccess": false,
"isChatResourceSpecificConsentEnabled": true
}Using PowerShell
Installing the Microsoft Graph PowerShell SDK
To use the Microsoft Graph PowerShell SDK module, you have to install it first. Alternatively, if you have Azure Cloud Shell set up, you can skip the installation step because it has the required module already installed.

Connecting to Graph
After installing, you have to change the Graph endpoint to the beta endpoint.
Select-MgProfile -Name 'beta'
Now you are going to import the required submodule.
Import-Module Microsoft.Graph.Teams
To configure the following settings, you have to specifically grant the required permissions to the Microsoft Graph PowerShell app in your AAD. You should be able to find the app easily using its App ID: 14d82eec-204b-4c2f-b7e8-296a70dab67e The required permission is TeamworkAppSettings.ReadWrite.All.
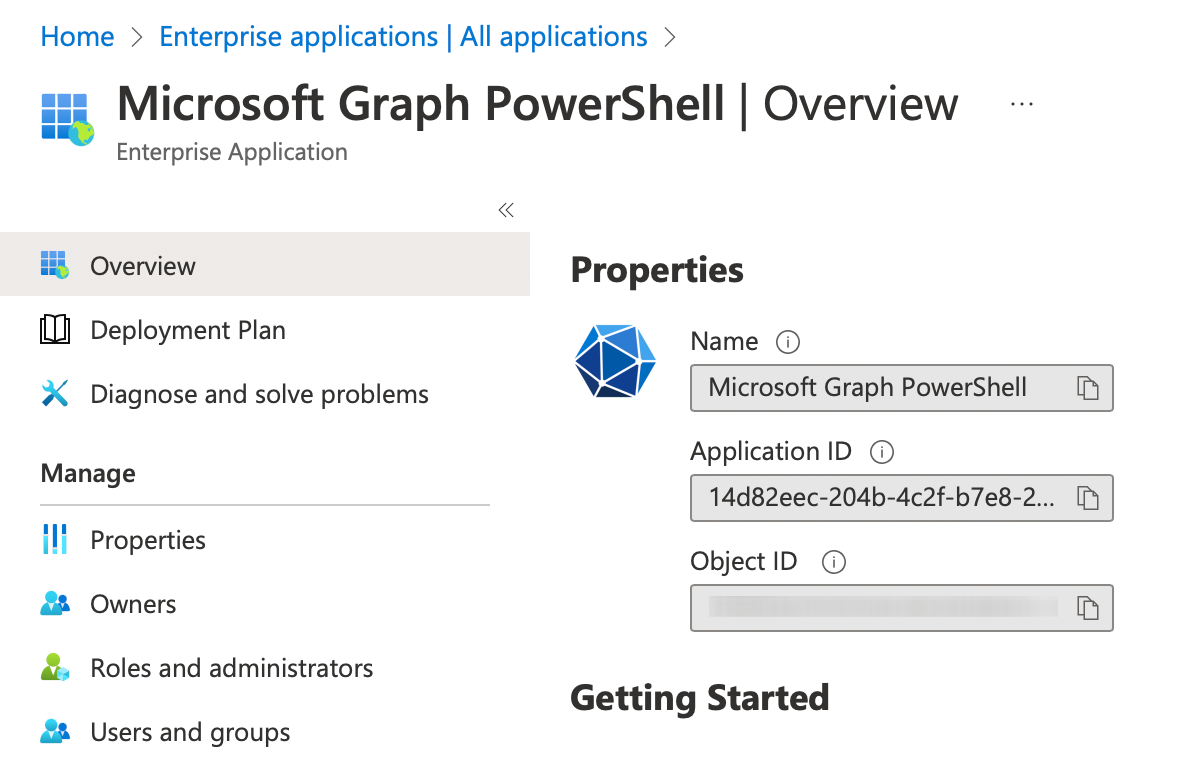
After granting the required permission, we can connect to Graph:
Connect-MgGraph -Scopes TeamworkAppSettings.ReadWrite.AllFirst we check the current configuration with the following cmdlet:
Get-MgTeamworkTeamAppSetting | fl *Id : ...
IsChatResourceSpecificConsentEnabled : True
AdditionalProperties : {[@odata.context,
https://graph.microsoft.com/beta/$metadata#teamwork/teamsAppSettings/$entity],
[allowUserRequestsForAppAccess, True]}The relevant setting is [allowUserRequestsForAppAccess, True].
To disable user requests and consequentially hide blocked apps in the Teams app store, we need to set the bool value to false with the following commands:
$params = @{
"@odata.type" = "#microsoft.graph.teamsAppSettings"
AllowUserRequestsForAppAccess = "false"
}Update-MgTeamworkTeamAppSetting -BodyParameter $paramsTo validate if the configuration was successful, simply run the Get-MgTeamworkTeamAppSetting cmdlet again.
Id : ...
IsChatResourceSpecificConsentEnabled : True
AdditionalProperties : {[@odata.context,
https://graph.microsoft.com/beta/$metadata#teamwork/teamsAppSettings/$entity],
[allowUserRequestsForAppAccess, False]}After validation, we properly disconnect from Graph.
Disconnect-MgGraphThat's it! The blocked apps should now start disappearing from the Teams app store. In my dev environment, it took around 45 minutes to see the change reflected in Teams clients.
Sources
- Update teamsAppSettings - Microsoft Graph beta | Microsoft Learn
- Update-MgTeamworkTeamAppSetting (Microsoft.Graph.Teams) | Microsoft Learn
- Graph Explorer | Try Microsoft Graph APIs - Microsoft Graph
- Azure Cloud Shell overview | Microsoft Learn
- Install the Microsoft Graph PowerShell SDK | Microsoft Learn